CytoSMART devices are connected to the Microsoft Azure cloud environment
Adopting cloud-based working allows those working in research to accelerate their work and save time, money, and effort. Unlimited data storage and fast computing time make the cloud far superior to any standard desktop computer.
As researchers ourselves, CytoSMART knows this, which is why our devices are now compatible with the Microsoft Azure cloud environment. Users can now archive and manage their data in a secure environment; accessible anywhere, instantly.
Given the often sensitive nature of the data our customers handle, our adopted protocol is based on three pillars:
- Data security
- Privacy
- Compliance with international regulations
Why use a cloud solution?
Opting for cloud computing is a huge innovative change, but why use an online solution? Our devices are connected to the cloud for several reasons.
Data is stored rapidly with an unlimited capacity
Our devices can potentially generate enormous amounts of data. The CytoSMART Omni allows users to create time-lapse videos of whole-wells in multi-well plates. A single scan consists of over 6500 cell-level photos that are automatically stitched together and analyzed.
The amount of data collected during just a single experiment, even if it only consists of a few scans, adds up quickly. All that data needs to be processed, analyzed, and stored somewhere secure and accessible: this is what the cloud provides.
A cloud instance offers a solution to store and process all of the data, without the need to set up an expensive server internally or rely on data storage technology.
Computing speed is increased, allowing for more efficient data processing
Image analysis allows the extraction of complex data from simple time-lapse videos. Cell proliferation, cell migration, and colony formation can all be calculated from time-lapse imaging. If these quantifications were to be done manually, this would take an enormous amount of time, leaving potential room for an increased margin of error.
Even where heavily optimized and compressed algorithms are deployed, big data needs high-performance computing. In the cloud, computational 'assignments' are split up and performed in parallel, with each assignment solving a fraction of the puzzle concurrently, reducing the overall time elapsed.
The cloud brings together an army of high-performance, high-speed machines to process your data without the need to purchase, store, or staff those machines on site.
Cloud-powered devices can be accessed remotely, so you really can work anywhere
Research doesn’t just happen in the science lab. Whether you’re in your office, at home on your phone, or somewhere else, you’re probably monitoring your cells and observing experiment progress pretty regularly.
This can be highly beneficial for specialized labs such as BSL-3/4 laboratories, but also in the new social distancing situation, we find ourselves in. If you don’t have to be in the lab to perform routine checks - observing confluency or morphology - then your co-workers can be in the lab instead, carrying out changes and driving the tests forward.
----------------
Remote working is particularly beneficial for BSL-3/4 labs, find out why in our recent article on labs and remote working.
-----------------
Why store in the cloud?
Storing your data in the cloud means you have remote access you can trust to stay live and secure, without maintaining your own servers.
The case for deploying the cloud should be clear by now, but what are the perceived drawbacks of a cloud-based approach?
One thing you’re probably concerned about is data protection, given the sensitive nature of some of the data you likely store. Loss of, or breach of data would be detrimental and should be avoided.
Trust your cloud
Cloud services are becoming increasingly accepted and provide efficient solutions to manage professional security needs. They simplify net configuration, ensuring reliability and availability of services, and provide automatic data-backup functionality.
Multiple layers of protection
CytoSMART has solutions to guarantee security. To ensure you can work in a safe environment we have developed a protocol for data protection, based on a strategy founded on multiple layers of protection.
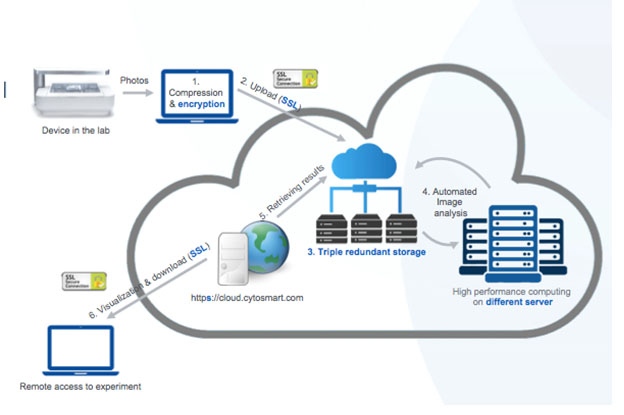
Upload and download protected, through Secure Socket Layer (SSL)
Both the upload and the download of your data go through Secure Socket Layer. This technology ensures connection security and protects the exchanged sensitive data. It prevents unauthorized third parties from intercepting or modifying the transferred information. As shown above, data is encrypted and can only be read in the cloud, where the decoding key is stored.
Encryption of the data
CytoSMART uses cryptography to protect all data. Encryption ensures that the data can only be read in the cloud, where the decoding key is stored. This safeguards information and is the simplest way to guarantee that it cannot be stolen. It also proves that the information is authentic and derives from our database.
Data is never lost
CytoSMART has triple-redundant storage – which helps to prevent eventual liabilities in protection that could cause disruption or loss of data. Should a server failure occur, there are always 2 backups available. The stored data cannot be modified and the original data is always stored on a separate server.
Regular checks to software integrity
Software updates are imperative to ensure your data’s safety. You may regularly click “remind later,” when your desktop or mobile device mentions an update, but we don’t.
In order to continuously improve our image analysis software, our software engineers perform extensive checks and software updates. This is to ensure the user experience is always smooth and your data and imagery are always completely secure and not compromised.
With ethical hacking (a real cyber-attack performed by an independent third party to evaluate your system’s security), we are continuously ensuring that our systems are as secure as we say they are.
Penetration testing is performed on a yearly basis, ensuring we are instantly aware of any weaknesses in our cloud systems, before they affect you (the user).
We are delighted that, during our most recent ethical hacking drills, our cloud was unreachable.
Reinforced protocol through the Microsoft Azure System
Despite the strength of all the above-mentioned strategies we are not satisfied that the sum of all measures is enough. We consider data security the highest priority and to further strengthen our protocol, we have teamed up with Microsoft Azure to create a system impervious to hacking.
What is Microsoft Azure?
Microsoft Azure is a cloud computing service created for building, testing, deploying, and managing applications and services through extremely secure Microsoft-managed data centers.
With over $1bn invested in research and development of security themes by the Azure team, there’s no better service for us to collaborate with in terms of security.
With more than 90 compliance certificates held by Microsoft Azure, it’s no surprise that they are consistently keeping governments, authorities, regulatory bodies, and non-governmental organizations protected and secure. For us, there was no better service to team up with.
Not only does this improve security in your immediate vicinity, with Microsoft Azure, we can guarantee you are compliant globally. This future-proofs your business for any growth or legalities that may occur going forward.
How is CytoSMART’s cloud privacy controlled, we hear you ask?
We want to provide you with the best tools to work in a secure environment yet, we also comprehend the need to have a private environment.
Cloud privacy is controlled by the following standards:
1. We make sure that your personal data are protected, respecting GDPR guidelines.
2. The data you create with our devices is controlled by you only, in your own environment.
To provide added protection, we also give our users the following tools:
- Data access by logging into a protected environment using the personal account information (email + password)
- The ability to invite people to access data via a share button
- Complete ownership of all data - CytoSMART will never own the content you store in the cloud, and can therefore never use it for advertising or marketing purposes
- The ability to add or remove users if you have administrator rights
- Easily organized data using the folder structure of projects and experiments
We take care of your data
Naturally, all research data is precious. Acquiring data is time-consuming and expensive. We believe that a cloud solution provides many advantages and is a secure option.
Related Products
There are currently no products tagged to this resource.